
 |
|
|
|
Stuxnet Virus CIA & Mossad v. Iran Reactors - Flickr Photos 21/4/14 |
|
CIA RQ -170 Iran - RQ 170 - Flickr Photos |
|
DailyMotion Ex. Iran official Talk on US Sabotage of Iran Bomb 20/4/14 |
|
DailyMotion Iran Atom Dr. How Stuxnet Virus Strikes Reactors 19/4/14 |
 |
 |
 |
|
|

China`s Official People`s Daily English Audio China Time 10:50 , April 26, 2011 : Iran detects another cyber attack The computer worm of "Stuxnet" infected 30,000 IP addresses in Iran |
|
|
 |
|
|
 |
|
|
|
|
| Iran accuses Siemens over Stuxnet
virus attack
Sun Apr 17, 2011 11:25am GMT * Military commander urges action against German company * Siemens control systems hit by virus * Stuxnet dubbed world's first "guided cyber missile" TEHRAN, April 17 (Reuters) - An Iranian military commander has accused German engineering company Siemens of helping the United States and Israel launch a cyber attack on its nuclear facilities, Kayhan daily reported on Sunday. Gholamreza Jalali, head of Iran's civilian defence, said the Stuxnet virus aimed at Iran's atomic programme was the work of its two biggest foes and that the German company must take some of the blame. Siemens declined to comment. "The investigations show the source of the Stuxnet virus originated in America and the Zionist regime," Jalali was quoted as saying. Jalali said Iran should hold Siemens responsible for the fact that its control systems used to operate complicated factory machinery -- known as Supervisory Control and Data Acquisition (SCADA) -- had been hit by the worm. "Our executive officials should legally follow up the case of Siemens SCADA software which prepared the ground for the Stuxnet virus," he said. "The Siemens company must be held accountable and explain how and why it provided the enemies with the information about the codes of SCADA software and paved the way for a cyber attack against us," he said. Some foreign experts have described Stuxnet as a "guided cyber missile" aimed at Iran's atomic programme. Unlike other Iranian officials who have played down the impact of Stuxnet, Jalali said it could have posed a major risk had it not been discovered and dealt with before any major damage was done. "This was a hostile act against us which could have brought major human and material damages had it not been encountered promptly." Iran has given few details of the impact of the virus. It said in September that staff computers at the Russian-built Bushehr nuclear power station had been hit but that the plant itself was unharmed. Bushehr -- Iran's first nuclear power station -- is still not operational, having missed several start-up deadlines, prompting speculation that it too had been hit by Stuxnet, something Iran denies. Russia's ambassador to NATO said in January the virus had hit the computer system at Bushehr, posing the risk of a nuclear disaster on the scale of the 1986 Chernobyl incident in Ukraine, then part of the Soviet Union. Some defence analysts say the main target was more likely to be Iran's uranium enrichment -- the process which creates fuel for nuclear power plants or provide material for bombs if processed much further. Western powers accuse Iran, a major oil producer, of seeking to develop nuclear weapons capability, something Tehran denies. U.S.-based think-tank, the Institute for Science and International Security (ISIS), said that in late 2009 or early 2010 about 1,000 centrifuges -- machines used to refine uranium -- out of the 9,000 used at Iran's Natanz enrichment plant, had been knocked out by the virus -- not enough to seriously harm its operations. |
 |
|
|
| US, Israel 'behind Stuxnet'
virus: Iran officer
(AFP) 16/4/11 TEHRAN — The United States and Israel are behind the computer worm Stuxnet designed to hurt Iran's controversial nuclear programme, state news agency IRNA reported Saturday quoting a military officer. Jalali was the first Iranian official to accuse Tehran's two arch-foes over the Stuxnet virus. German computer experts and some Western media reports had indicated that the United States and Israel were behind it. Stuxnet was publically identified last June and it reportedly mutated and wreaked havoc on computerised industrial equipment in Iran in the following months. The worm was reportedly targeting Bushehr nuclear power plant, where several technical problems have been blamed for delays in getting the facility fully operational. Jalali said once the worm mounts on a system, it begins to gather information and then sends reports from the infected machines to designated Internet addresses. "After following up the reports that were sent, it became clear that the final destinations (of these reports) were the Zionist regime and the American state of Texas," he was quoted as saying by IRNA. In March, a German computer security expert Ralph Langer said he believes the United States and Israel's Mossad had unleashed the Stuxnet worm on Iran's nuclear programme. But it was the New York Times which reported first in January that US and Israeli intelligence services collaborated to develop the computer worm to sabotage Iran's efforts to make a nuclear bomb. In November 2010, Iranian President Mahmoud Ahmadinejad admitted that uranium enrichment -- the most controversial part of Tehran's nuclear programme - had suffered problems caused by the malware but added the issues had been resolved. Iran's nuclear ambitions are at the heart of a conflict between Tehran and the West, which accuse the Islamic republic of seeking to develop a weapons capability under the cover of a civilian nuclear drive. |
 |
| Iranian Police Sets Up Cyber
Force
TEHRAN Fars News Agency (FNA) - Iran's Cyber Police started its work today to prevent espionage and sabotage activities through the internet, a police official announced on Sunday 2011-01-23 17:22 "The Cyber Police can prevent espionage and sabotage in Information Technology (IT) tools," Head of the Information Production and Exchange Department of the Law Enforcement Police General Seyed Kamal Hadianfar said. Hadianfar reiterated that IT tools play an undeniable role in political, security, economic, trade, ethical and religious rivalries at the national and international levels. He also underlined that given the people's growing interest in using the internet, the threats and opportunities presented by the IT now need to be attended more than before in the country, adding that the governments should have plans for confronting these threats and using these opportunities. Earlier in 2009, Iran's Police Chief Brigadier General Esmail Ahmadi-Moqaddam had announced that the force plans to set up a 'cyber police' division to counter 'internet crimes'. Ahmadi-Moqaddam said the unit would be tasked with monitoring organized cyber crimes on the internet. Iran announced in March 2010 that it has arrested 30 individuals on charges of waging a US-backed cyber war against the country. A statement issued by Tehran's Public and Revolutionary Court at the time said that following a series of complicated security operations in area of information and communication technology, the country's security forces have identified the most important US-backed organized networks of cyber war launched by the anti-revolutionary groups and arrested 30 suspects. The statement added that the networks received US aids and served Washington through such anti-revolutionary groups as the Mojahedin-e Khalq Organization (MKO), monarchist groups and a number of other opposition groups. It further said that Washington provided such anti-Islamic Republic groups and networks with 70 million US-made anti-filtering software only during the recent demonstrations in Tehran in a bid to help them wage a psychological war against the Iranian nation and government. According to the statement, some of the charges leveled against these US-backed networks include establishment of an intelligence gathering network, specially to identify the country's nuclear scientists, provoking sedition and illegal demonstrations and rallies through releasing unreal and unfounded news and reports after the June presidential elections in the country and providing media and news support for the Jundollah terrorist group and the monarchist opposition groups. |
|
|
|
|
 |
 |
 |
 |
 |
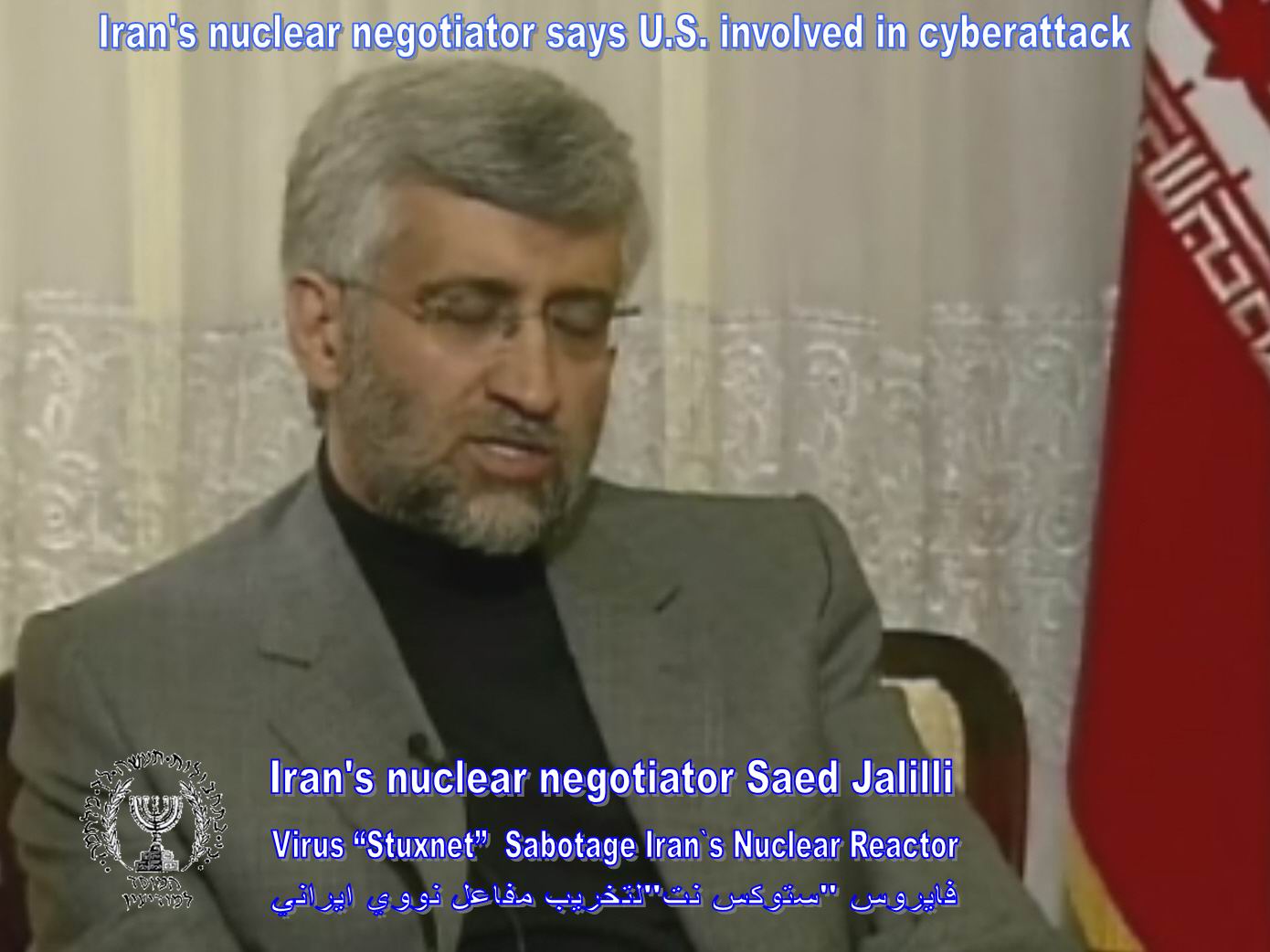
| Iran's nuclear negotiator says
U.S. involved in cyberattack
NBC News updated 1/17/2011 6:42:31 PM TEHRAN, Iran — Telegraphing Iran's
negotiating stance entering key talks about its nuclear program in Turkey
later this week, Tehran's chief negotiator is charging that the United
States was involved in a cyberattack that he said disrupted a peaceful
program aimed at creating nuclear energy, not weapons.
"I have witnessed some documents that show ... their satisfaction in that (the U.S. was involved)," he said. Jalilli indicated, however, that the cyberattack was not as successful as some media accounts have portrayed it. "Those who have done that could see now that they were not successful in that and we are following our success," he said. He added that Iran is not the only country vulnerable to cyberattacks, as evidenced by the WikiLeaks release of U.S. diplomatic cables. "They are also weak and vulnerable," he said of the United States. |
|
|
|
|
|
|
|
|
 |
 |
 |
 |
 |